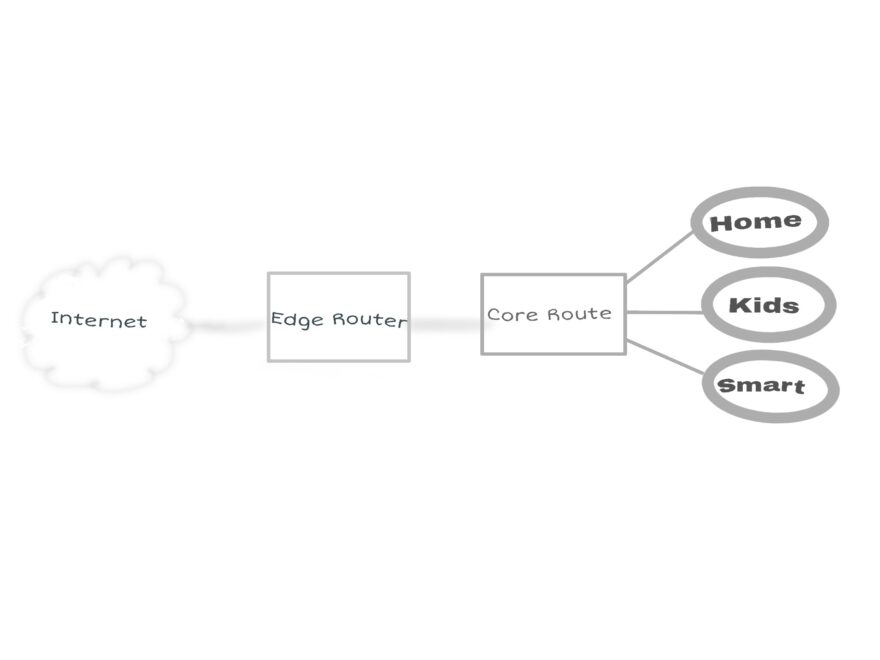
There is a very common routing issue, that might exist, when you are setting up your home network with the help of RFC1918 based IPv4 addresses. How to make sure that unassigned private IP address destinations will not be forwarded to the default gateway or public Internet.
Situation
Nowadays most of the Internet service providers – ISPs will push you into the situation that you have to consume their “specialized routers” to get access to the Internet. Commonly, those routers are in the control of your ISP and will be maintained via TR-069.
On the first view, this is nothing worse. They are aiming to offer a standardized and easy to use service. The big benefit: You don’t need to be worried about your router configuration.
On the second view, you need to understand that those routers are designed for the consumer segment and are mostly limited in their functionality. That’s not a surprise. Standardization will reduce complexity and the risk of failure. ISPs want to generate revenue. A reduced workload at the support and service hotline has got a positive impact on costs.
Well, I am personally feeling bad about this! The ISP does have access to my router. Ergo, they do have access to my network (somehow)!
Consequence
Choose the best of two worlds!
Proactively preventing endless discussions with my ISP’s hotline, e.g. in the situation of a line failure, I did take the router from my ISP. Let’s call the router an edge router or CPE. Yes, I know edge router is probably to much for a standard consumer router, well, never mind!
And to cover my enhanced demands, related to security and functionality, I introduced my own router. Let’s call the router a core router.
Introducing a second router will bring us in the situation that we need to take care about routing.
The problem
In consequence, the approach sending all IP requests, that do not belong to the local network (e.g. 192.168.0.0/24, 192.168.2.0/24 or 192.168.178.0/24), to the default gateway (the edge router facing the internet), needs reconsideration.
If everything is going well, the edge router is forwarding all requests to the Internet and will withdraw all requests to private RFC1918 addresses, that are not part of your home network.
Now things changed! You do have a core router in place, that represents your home network. Resulting in the situation that every traffic, that is not intended for public Internet destinations, is required to be forwarded to your core router.
Let’s assume that your home network is a 10.0.0.0/8 and the edge router has got the internal address 192.168.178.1/24. The core router is connected via 192.168.178.2/24 and is responsible for three network segments:
Home: 10.0.0.0/24
Kids: 10.0.1.0/24
Smart(home): 10.0.2.0/24Static route to your network
Network segments attached to the core router require a routing entry. This will be implement as demonstrated in the following picture. Currently, we don’t expect private IP addresses from another router. Therefore, in the current example, feel free to take the complete range: 10.0.0.0/8.
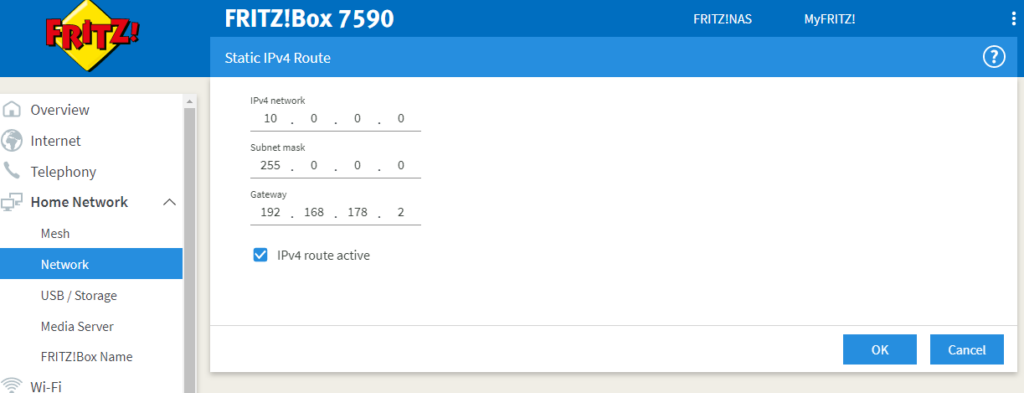
10.0.0.0/8 will be forwarded to the internal core router with the address 192.168.178.2. The default gateway
On the core router you need to take care, as well.
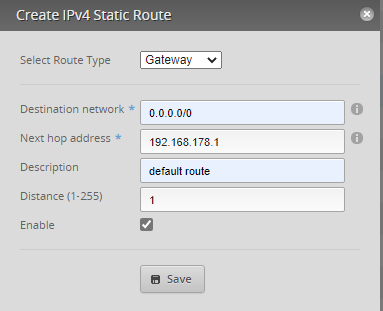
First, you have to make sure that everything that will not belong to your network is able to find the way into the Internet.
In this example we make use of an EdgeRouter™-X. Unfortunately, this might confuse you as the EdgeRouter™-X represents the core router.
In the graphical user interface – GUI you may configure your default gateway like in the example. Whereas 192.168.178.1 is representing the Fritz!Box (edge router) connecting the Internet.
If you prefer the command-line interface – CLI you may do it like this:
configure
set protocols static route 0.0.0.0/0 next-hop 192.168.172.1
commit
save
exit
Now we have reached a state where most stop with their configuration activities. Everything seems to be fine. You may reach the Internet. The Internet may reach you!!!
Firewall configured? Just asking for a friend!
If you’re interested to know howto delete a route using EdgeRouter™-X , you might find this post helpful: delete IPv6 route on EdgeRouter™-X
Playing ping-pong
Now we are able to demonstrate the problem itself:
- You are using your PC in the network segment Home with the IP address
10.0.0.123. - You want to configure a device in your Smarthome segment with the IP address
10.0.2.200.
By mistake you entered 10.0.20.200, to reach the device.
What happens?
Usually, your PC will query your core router, to find the right way into the Smart(home) network segment:
from: 10.0.0.123 via 10.0.0.1 (gateway home - directly connected with core router)
forward to: 10.0.2.1 (gateway smart - directly connect with core router)
forward to: 10.0.2.200
The mistake will lead to another situation:
from: 10.0.0.123 via 10.0.0.1 (gateway home - directly connected with core router)->
forward to: 192.168.178.1 (core router - I don't know a route to 10.0.20.200 - send to default gateway)
forward to 192.168.178.2 (edge router - I do have a static route for 10.0.0.0/8 - send to core router)
forward to: 192.168.178.1 (core router - I don't know a route to 10.0.20.200 - send to default gateway)
forward to 192.168.178.2 (edge router - I do have a static route for 10.0.0.0/8 - send to core router)
forward to: 192.168.178.1 (core router - I don't know a route to 10.0.20.200 - send to default gateway)
forward to 192.168.178.2 (edge router - I do have a static route for 10.0.0.0/8 - send to core router)
...
Just for clarity, this example is just for illustration.
If you are working with big enterprises, this might sound familiar. Everyone has got an idea who might be in charge. But no one feels responsible. Ever heard about “The Twelve Tasks of Asterix”?
Taking ownership
Let’s recap:
- no destination with a private IP address will be in the Internet (well, maybe)
- no forwarding for private addresses to the default gateway – edge router
- the core router must be aware of his responsibilities – e.g. ownership of
10.0.0.0/8
In our situation, the core route is just aware of the direct connected network segments: 10.0.0.0/24, 10.0.1.0/24 and 10.0.2.0/24. And this is the root cause of the confusion.
How may we enable the core router to be aware about his ownership?
Black hole routing or null routing
Black hole routing will advise the router to withdraw all related requests. Imagine this as a routing to /dev/null.
In our example we do have the situation that the target address 10.0.20.200 does not exist and is forwarded to the default gateway. This can be prevented with the following configuration:
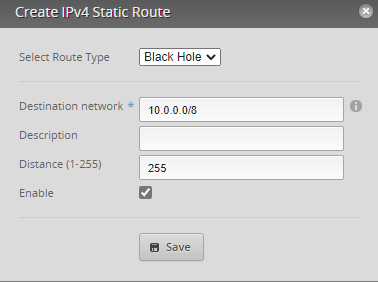
If you prefer the command-line interface – CLI you may do it like this:
configure
set protocols static route 10.0.0.0/8 blackhole distance 255
commit
save
exit
No worries!
Reading this you might be a bit frightened. Sending everything for 10.0.0.0/8 to null will affect your local networks, as well.
Let’s have a look!
show ip route
...
S *> 10.0.0.0/8 [255/0] is a summary, Null
C *> 10.0.0.0/24 is directly connected, eth1
C *> 10.0.1.0/24 is directly connected, eth2
C *> 10.0.2.0/24 is directly connected, eth3
...
Usually, the routing table is applied in order from most specific to least specific. This means, the entries for our three network segments will be considered first. As there’s no match for 10.0.20.200, the next valid match is the 10.0.0.0/8.
And to be perfectly sure, there is a distance parameter. As our three network segments are directly connected, they do have the shortest possible distance. For our least specific rule 10.0.0.0/8, a distance of 255 [1-255] has been configured. This means, even if there would be a conflicting rule, the high distance will make sure it’s considered last.
In consequence this will make it quite easy, as we do not need to exclude network ranges.
So finally, a configuration of…
set protocols static route 10.0.0.0/8 blackhole distance 255
set protocols static route 172.16.0.0/12 blackhole distance 255
set protocols static route 192.168.0.0/16 blackhole distance 255
…will make sure that nothing will be forwarded to the edge router, that is a private network address destination and is not part of our defined network segments.
In addition you may include the fc00::/7 ULA address range into your IPv6 routing table:
set protocols static route6 'fc00::/7' blackhole
Appendix
Of course, it’s possible to send single IP addresses to a blackhole route, as well. This is quite a good method to ignore unwanted hosts, attackers and suspicious services.
E.g.:
set protocols static route 8.8.4.4/32 blackhole distance 1
set protocols static route 8.8.8.8/32 blackhole distance 1
set protocols static route6 '2001:4860:4860::8844/128' blackhole distance 1
set protocols static route6 '2001:4860:4860::8888/128' blackhole distance 1
Why exactly this example? Probably in another post about my kids tablets.
…