Google DNS server in my Kindle configuration, seriously?
Configuring my Kindle network configuration, I observed something spooky. Despite using DHCP and my own network services, there appeared the Google DNS server address 8.8.8.8 in the network configuration, always.
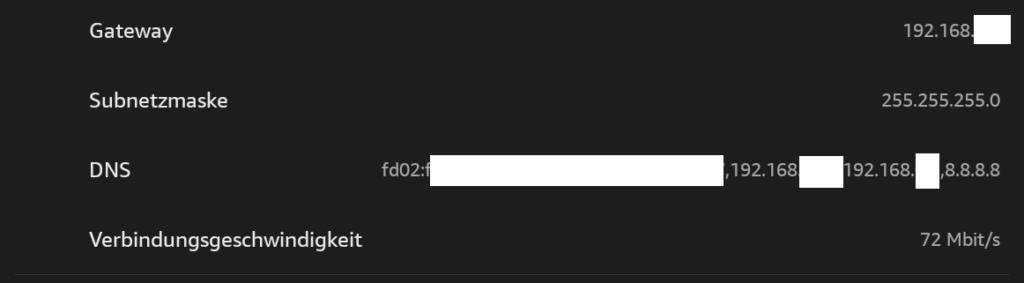
Doing some research in the Internet, I’m not alone!
E.g.: Kindle Fire HD 10 9th gen is adding a dns server on its own. | XDA Forums (xda-developers.com)
Well, think about this: Despite I’m providing my own network and DNS server configuration using DHCP, the Google DNS server appears in the Kindle configuration, always!
I’m not amused! This is an attack on a sovereign state!
For a good reason, I make use of my own DNS server. We do have a wide range of tablets and media devices in my family. And my kids start to make use of them.
Therefore, I’ve implemented a DNS server, based on the Pi-hole project. E.g. Pi-hole will enable me to define allow- and deny lists, with the help off regular expressions. E.g. this will give me the freedom to control unsafe content, block adds and chatty devices. And there’re many more good reasons to provide your own DNS server.
Always providing a foreign DNS server in the network configuration is unacceptable!
How to get this sorted?
Based on the discussion in the Internet, there’s no easy way to remove the configuration. And maybe, on the next update or upgrade the configuration will reappear. I do have a big bunch of different devices, I need a centrally managed solution.
Thank good, I do have a core router with advanced functionality. Maybe, my other post about black hole routing came to your attention? In the mentioned post, the solution is perfectly described.
I configured my core router to send all requests affecting Google DNS servers into a black hole/null aka. /dev/null.
set protocols static route 8.8.4.4/32 blackhole distance 1
set protocols static route 8.8.8.8/32 blackhole distance 1
set protocols static route6 '2001:4860:4860::8844/128' blackhole distance 1
set protocols static route6 '2001:4860:4860::8888/128' blackhole distance 1
Bye-bye! Google DNS server…
Quite a good summary of the different syntax for black hole routing, e.g. BSD, Linux, IOS and Windows you may find here: http://blog.up-link.ro/how-to-add-a-nullroute-blackhole-filtering/
Why not using firewall rules?
Yes, indeed! It’s a good idea to block all outgoing traffic on port 53 (TCP/UDP). Exception on your own DNS server and forwarder, of course.
Routing is less CPU expensive than firewalling, and you can’t be sure it will be port 53, always. I chose this way, in addition.
