To install OpenWrt on your TP-Link EAP245 v1, you may follow the instructions at the OpenWrt Git.
As I was a newbie with OpenWrt, it was quite tough to follow the instructions. This inspired my to write an additional how-to. I hope you may find this useful.
Download OpenWrt installation firmware
- Go to the specific OpenWrt Wiki page for the TP-Link EAP245 v1
- Download the “Firmware OpenWrt install” – squashfs-factory
Start telnetd
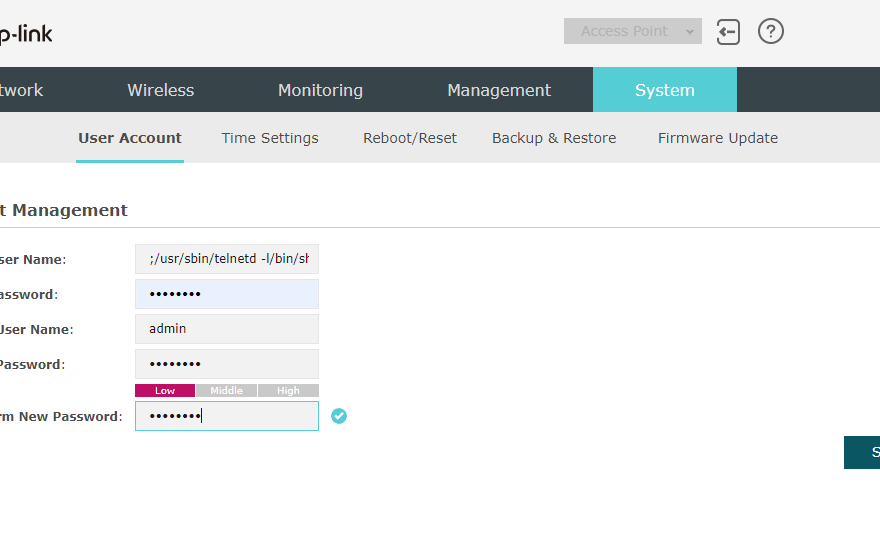
To start the telnetd daemon you need to exploit the username. To do this, login into the Web interface and and select the System -> User Account section. As an alternative, I did reset the access point. Once done, you’ll be asked to define a new username and password.
Exploit username
As explained in the OpenWrt Wiki, create a new username:
;/usr/sbin/telnetd -l/bin/sh&
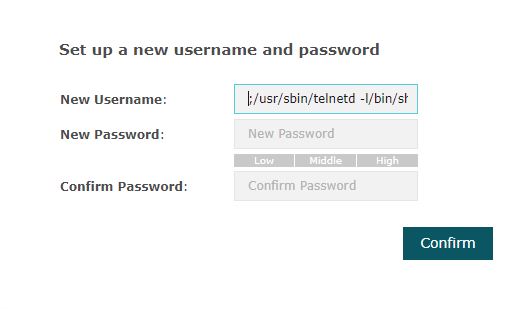
Change exploited username to admin
Once done, revert the username to e.g. admin
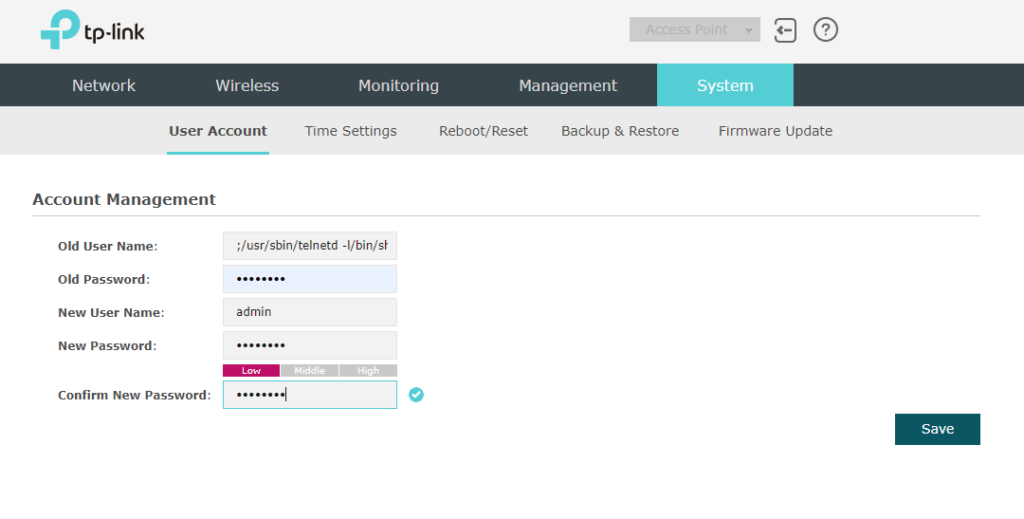
Connect to root shell
Chose your preferred telnet client, e.g. putty, to connect with the access point.
- Use the username and password defined before.
Prepare for the installation
To install OpenWrt, some preparation is required
chmod /tmp
Execute the following command
chmod 777 /tmp -R
validate
# ls -la | grep tmp
drwxrwxrwx 3 0 0 0 Jan 1 00:01 tmp
Download uclited
To patch uclited, copy it to your local system.
/usr/bin/uclited
I had some issue to copy the file from my client. So I copied the file, from the access point, to a remote host with the help of scp. In my case a raspberry…
# scp /usr/bin/uclited pi@192.168.0.123:/home/pi/
Patch uclited
cp /home/pi/uclited /home/pi/uclited-patched
Download the file to your local pc and open the file in e.g. Notepad++
PS E:\OpenWRT\EAP245> scp pi@192.168.0.123:/home/pi/uclited-patched .
Make sure the HEX-Editor plugin for Noteapad++ is installed in Plugins Admin
Got to address 000d2260
Replace
-000d2260: 8c44 0000 0c13 45e0 27a7 0018 8fbc 0010
+000d2260: 8c44 0000 2402 0000 0000 0000 8fbc 0010
Upload the patched file to your linux host
PS E:\OpenWRT\EAP245> scp .\uclited-patched pi@192.168.0.123:/home/pi/uclited
Rename squashfs-factory file
Rename openwrt-21.02.0-ath79-generic-tplink_eap245-v1-squashfs-factory.bin to upgrade.bin
Upload to linux host
PS E:\OpenWRT\EAP245> scp .\upgrade.bin pi@192.168.0.123:/home/pi/
Copy files to access point from access point
# scp pi@192.168.0.123:/home/pi/uclited /tmp/
# scp pi@192.168.0.123:/home/pi/upgrade.bin /tmp/
Start the installation
# chmod +x /tmp/uclited && /tmp/uclited -u
Begin Debug Mode Fireware Upgrade
Upgrade fireware size is 5604743 bytes
Upgrade fireware md5 checksum is correct!
Now upgrade fireware...
######################################################################
####################
Done.
Firmware upgrade successfully! Please reboot manually.